Thank you, It’s really useful.
Hidden switches of Certutil.exe and Certreq.exe
Hey Kids, Rock and Roll!
Two of the most reliable toolsets in Windows for the last two decades have been the tandem of certutil.exe and certreq.exe. It’s no secret there are a wealth of very useful functions exposed in the basic usage of these tools, also documented publicly here:
certutil.exe public documentation
certreq.exe public documentation
But what is not as widely known are the hidden switches of certutil.exe and certreq.exe. In order to expose these, the following case-sensitive syntax is needed:
certutil.exe -uSAGE certreq.exe -uSAGE
These can be expanded fully with the -v switch preceding the –uSAGE switch, for example:
certutil.exe -v -uSAGE
Each hidden switch can also be fully expanded in this fashion. Let’s take a look at some of the differences. We’ll start with certutil.exe.
In order to visually see the differences I piped the regular -? output alongside the –uSAGE output and used the Compare plugin in Notepad++ to see the deltas.
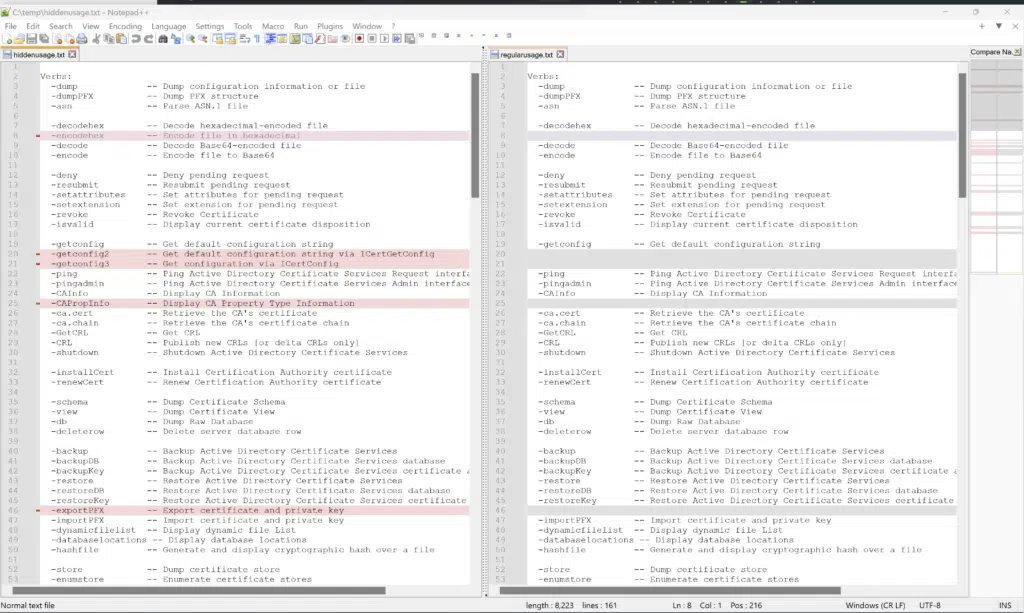
Output of certutil -uSAGE on the left and certutil -? on the right
Immediately you notice there are several included in –uSAGE not included in –?
Here are the differences for certutil.exe:
-encodehex -- Encode file in hexadecimal -getconfig2 -- Get default configuration string via ICertGetConfig -getconfig3 -- Get configuration via ICertConfig -CAPropInfo -- Display CA Property Type Information -exportPFX -- Export certificate and private key -TPMInfo -- Display Trusted Platform Module Information -getcert -- Select a certificate from a selection UI -ds -- Display DS DNs -dsDel -- Delete DS DNs -dsCert -- Display DS Certificates -dsCRL -- Display DS CRLs -dsDeltaCRL -- Display DS Delta CRLs -dsTemplate -- Display DS Template Attributes -dsAddTemplate -- Add DS Templates -SetCATemplates -- Set templates for CA -URL -- Verify Certificate or CRL URLs -SCDump -- Dump smart card file information -key -- List key containers -delkey -- Delete named key container -csplist -- List CSPs installed on this machine -csptest -- Test CSPs installed on this machine -CNGConfig -- Display CNG Configuration -Class -- Display COM registry information -7f -- Check certificate for 0x7f length encodings -getsmtpinfo -- Get SMTP info -setsmtpinfo -- Set SMTP info
Each of these differences can be individually articulated, for example:
certutil.exe -csplist -?
or fully articulated
certutil.exe -csplist -?
It usually isn’t much difference, but it helps show a number of the possibilities.
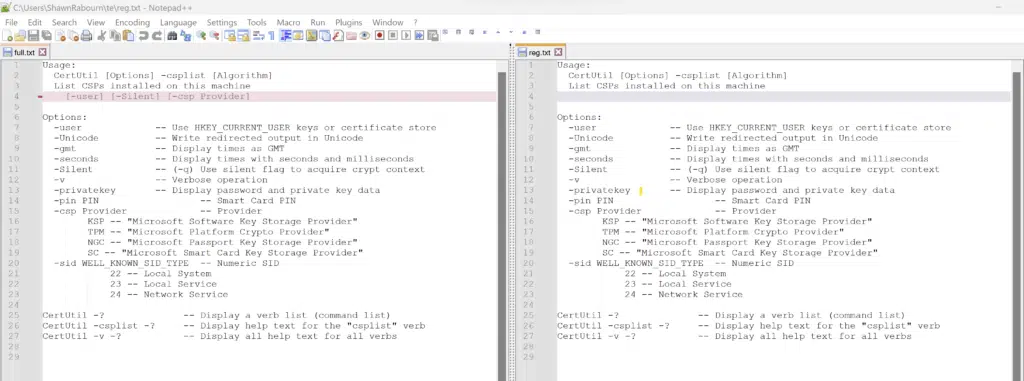
Verbose help output for certutil -csplist on the left, regular output on the right
There are several switches which are immensely helpful in performing operations and troubleshooting. The –ds switch can be used to show what the Active Directory containers look like. The –dstemplate switch can be used to enumerate a particular certificate template. If you throw a –v before –dstemplate it can be used to fully articulate the template and expand enrollment and private key flags. The – csplist and –csptest flags enumerate and test the legacy Cryptographic Service Providers as well as the Key Storage Providers on the computer. Those are immensely helpful in troubleshooting HSMs or Smart Cards and enumerating the Cryptographic Algorithms exposed by each provider.
Here are the hidden flags for certreq.exe:
CertReq -EOBO [Options]
Start the Enroll-On-Behalf-Of wizard.
CertReq -EnrollX [Options]
Enroll for multiple certificates.
Options:
-user
-machine
CertReq -AutoEnroll [Options]
Start Auto-Enroll U/I.
Options:
-v
-user
-machine
CertReq -Request [Options]
Create a custom request.
Options:
-user
-machine
CertReq -ImportPFX [Options] PFXFile [Provider [Reader [ContainerPrefix [FriendlyName [Flags]]]]]
Import PFX to specified provider.
Options:
-f
-q
-p Password
-pin Pin
-user | -machin
While it is interesting that certutil.exe has a hidden –exportPFX and certreq.exe has a hidden –ImportPFX, I must qualify posting these by saying “Use at your own risk”. They are hidden, and not documented for a reason.
There is also an –importPFX in the public switches for certutil.exe which seem to be vastly different than certreq.exe but with the potential for similar outcome.
certutil -v -importpfx -?
Usage:
CertUtil [Options] -importPFX [CertificateStoreName] PFXFile [Modifiers]
Import certificate and private key
CertificateStoreName -- Certificate store name. See -store.
PFXFile -- PFX file to be imported
Modifiers -- Comma separated list of one or more of the following:
AT_SIGNATURE -- Change the KeySpec to Signature
AT_KEYEXCHANGE -- Change the KeySpec to Key Exchange
NoExport -- Make the private key non-exportable
NoCert -- Do not import the certificate
NoChain -- Do not import the certificate chain
NoRoot -- Do not import the root certificate
Protect -- Protect keys with password
NoProtect -- Do not password protect keys
Defaults to personal machine store.
[-f] [-Enterprise] [-user] [-GroupPolicy] [-Silent] [-p Password] [-csp Provider]
Modifiers:
NoExport
ExportEncrypted
NoCert
NoChain -- End Entity certificate only
NoRoot -- Exclude root certificate
NoProtect
Protect
ProtectHigh
Pkcs8
AT_SIGNATURE
AT_KEYEXCHANGE
FriendlyName=
KeyFriendlyName=
KeyDescription=
VSM
Options:
-f -- Force overwrite
-Enterprise -- (-ent) Use local machine Enterprise registry certificate store
-user -- Use HKEY_CURRENT_USER keys or certificate store
-GroupPolicy -- (-gp) Use Group Policy certificate store
-Unicode -- Write redirected output in Unicode
-gmt -- Display times as GMT
-seconds -- Display times with seconds and milliseconds
-Silent -- (-q) Use silent flag to acquire crypt context
-v -- Verbose operation
-privatekey -- Display password and private key data
-pin PIN -- Smart Card PIN
-p Password -- Password
-csp Provider -- Provider
KSP -- "Microsoft Software Key Storage Provider"
TPM -- "Microsoft Platform Crypto Provider"
NGC -- "Microsoft Passport Key Storage Provider"
SC -- "Microsoft Smart Card Key Storage Provider"
-sid WELL_KNOWN_SID_TYPE -- Numeric SID
22 -- Local System
23 -- Local Service
24 -- Network Service
Contrast the usage above with certreq.exe
certreq -v -importpfx -?
Usage:
CertReq -?
CertReq [-v] -?
CertReq [-Command] -?
CertReq -ImportPFX [Options] PFXFile [Provider [Reader [ContainerPrefix [FriendlyName [Flags]]]]]
Import PFX to specified provider.
Options:
-f
-q
-p Password
-pin Pin
-user | -machine
Description:
-any - Force ICertRequest::Submit to determine encoding
type
-attrib AttributeString - Request attribute string
-binary - Output files in binary format instead of Base64-
encoded
-config ConfigString - Server\CertificationAuthority
or for an https: connection: Enrollment Server URL
or for a SCEP server: Server Name or URL
or use a single minus sign (-) for local machine CA
-crl - Include CRLs in CertChainFileOut or
RequestFileOut
-rpc - Use RPC instead of a DCOM server connection
-f - Force existing files to be overwritten
-q - Suppress all interactive dialogs
-v - Display full response properties
-? - Display this usage message
-Unicode - Write redirected output in Unicode
-UnicodeText - Write output file in Unicode
RequestFileIn - Base64-encoded or binary input file name:
PKCS10 certificate request,
CMS certificate request,
PKCS7 certificate renewal request,
X.509 certificate to be cross-certified, or
KeyGen tag format certificate request
RequestFileOut - Base64-encoded output file name
PKCS10FileOut - Base64-encoded PKCS10 output file name
CertFileOut - Base64-encoded X-509 file name
CertChainFileOut - Base64-encoded PKCS7 file name
FullResponseFileOut - Base64-encoded Full Response file name
ConfigString - Backslash separated server name and Certification
Authority name: MachineDnsName\CAName
AttributeString - Colon separated Name and Value string pairs
Each pair is separated by a backslash and "n"
Example: "Name1: Value1\n Name2: Value2"
PolicyFileIn - INF file containing a textual representation
of extensions used to qualify a request
Very interesting stuff. It is probably really easy to get the two mixed up if you typed them differently. Again, I reiterate: Use this information at your own risk.
I welcome comments regarding how people out there are using the undocumented switches in certutil.exe and certreq.exe. How are you using them?
Until next time…
Related Resources

Mark B. Cooper
President & Founder at PKI Solutions, Leading PKI Cybersecurity Subject Matter Expert, Author, Speaker, Trainer, Microsoft Certified Master.
View All Posts by Mark B. CooperComments
-
-
Intresting article, i appreciate it you shared it, and with your name it triggers me to ask you this question.
Are these hidden parameters in a relation with something i discovered from Windows 10 1709, can the hidden parameter sign c:\windows\servicing\trustedinstaller.exe with the same hash values even if it is different I noticed it uses the same hash value over a lot of different builds in windows 10 , but the sizes in different build differ. Then you expect different hash codes. Which maybe could be a problem when upgrade from one build to the other build. My only conclusion is that trustedinstaller itself is the ”root’ of all OS files and its itegrity. Cause it has more rights the the SYSTEM account. For sure legit Antivirus apps gets a token from this file/service to delete and recover files.
before i forget powercfg.exe got a hidden feature too try powercfg /q and then powercfg /qh it gives you acces too all sensors and powermanagement related settings in the windows os.
Greets
Mark Besselink

 Schedule a Demo
Schedule a Demo