Awesome, Vadims. Just fyi, I did some research and documentation on all the available Standard and Audit Events in the last years. These extend the Securing PKI whitepaper in terms of evaluating their relation to confidentiality, integrity and availability. Find them here: Standard Events (https://www.gradenegger.eu/?p=6183), Audit Events (https://www.gradenegger.eu/?p=6218). Perhaps you want to mention that some of the Standard Events only get logged when the LogLevel (https://www.gradenegger.eu/?p=528) has been increased, as well as Audit Events 4898, 4899 and 4900 only get logged when EDITF_AUDITCERTTEMPLATELOAD flag is set.
Enabling Active Directory Certificate Services (ADCS) advanced audit
Hello S-1-1-0, here is another unscheduled blog post on enabling advanced audit in Microsoft CA. Today I went through another thread on Twitter which suggests how to enable advanced audit in Microsoft CA. Throughout the thread it was apparent that only partial solution was provided.

Expand Your PKI Visibility
Discover why seeing is securing with revolutionary PKI monitoring and alerting.
Learn More About PKI Spotlight®Windows CA auditing engines
Microsoft CA implements a set of auditing engines, including:
- Standard Events — these are top-level informational events registered in Application event log. Such as CA certificate expiration notifications and relevant errors. Standard logging is enabled by default and does not require any configuration.
- Audit Events — these are detailed audit events registered in Security event log and display detailed activity in certificate services. Audit events are subject of this blog post. Audit events are not enabled by default.
- Debug Log — these are low-level debug traces logged in certocm.log, certutil.log and certsrv.log. These logs are useful only for Microsoft Support who can understand them. Debug log is not enabled by default.
Configuring CA Audit engine
Audit configuration in certificate services consist of two pieces:
CA\AuditFiltersetting in CA configurationObject Access Audit — Certificate Servicesin group policies.
First step is configured either, using certutil.exe or Certification Authority MMC (certsrv.msc), Audit tab. Here is the Microsoft article on configuring audit filter: Securing PKI: Appendix B: Certification Authority Audit Filter. In most cases it is configured simply as:
certutil –setreg CA\AuditFilter 127 net stop certsvc && net start certsvc
Don’t forget to restart certificate services, when configuring audit settings in Certification Authority MMC.
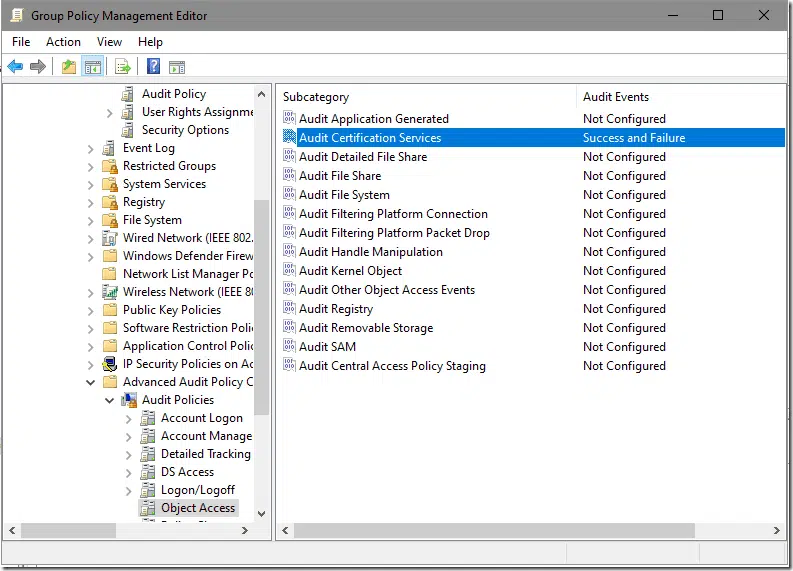
Second step requires GPO configuration, either, local (for workgroup members) or domain. It is configured with Success and Failure (this one is optional) under: Computer Configuration\Policies\Windows Settings\Security Settings\Advanced Audit Policy Configuration\Audit Policies\Audit Certification Services:
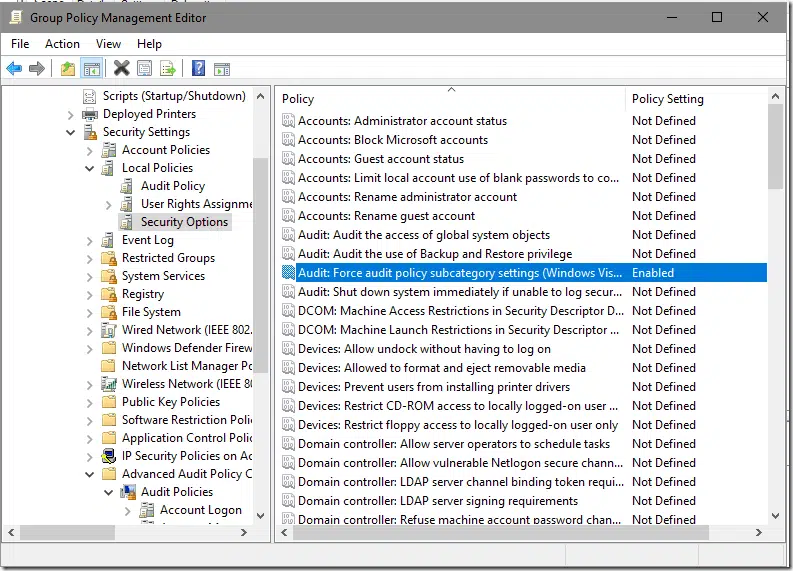
In addition, audit subcategory processing must be enabled under: Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Security Options\Audit: Force audit policy subcategory settings:
And apply the GPO to OU where CA servers reside and refresh policies on CA servers.
Verify Audit
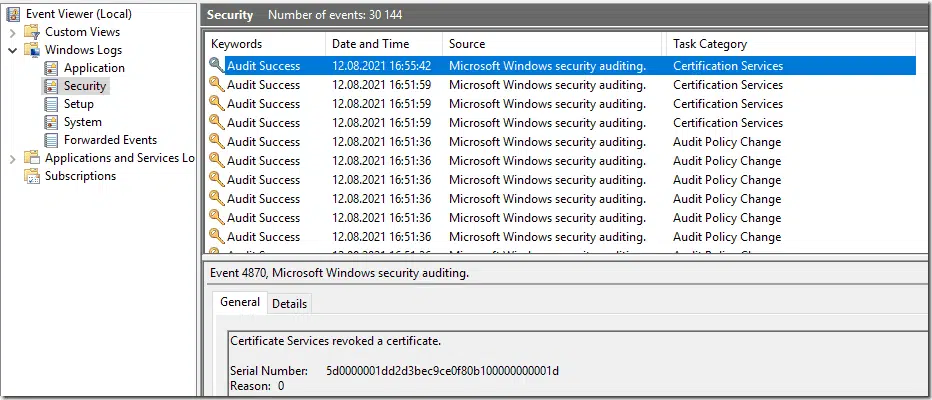
Only after all configurations are complete, events will start to show up in Security event log:
A full list of events registered by certificate services is provided in Securing PKI: Appendix A: Events to Monitor article.
HTH
Related Resources

Comments
-
-
I think it is a subject of more thorough document/whitepaper on eventing and auditing. Say, compose the information in different yours/mine/others blog posts, articles into a single and complete (to some extent of course) document. This blog posts focuses only on how to enable this logging. If you would like, we can cooperate on this and build a community whitepaper like I did in autoenrollment community whitepaper.
-
Hi Uwe, Do you have the English version of your articles? If you share that would be great. Thank you!
-
-
Nice article @Vadims! It might be worth mentioning that setting “Audit Policy Configuration” reverts all other Audit settings on the system (the Windows default Audit settings). All other settings (such as the default Logon/Logoff and other) are now in “No Audit” mode, effectively turning off a lot of settings that might be in use for other Audit purposes. I would recommend that you make an auditpol.exe /backup /file:xyz.csv on the standard configuration (the settings present on the CA server), import those settings to the GPO mentioned in this article and then change the “Certification Services” specific setting. I might be wrong, but this is how I remember it to work.
-
Hi John
You are right, the Advanced Auditing Policy is one of those policies that overwrite all other Advanced Auditing Policy policy settings from other GPOs or locally set.
Simplest approach is to use auditpol.exe to backup current policy settings of a server as a baseline and import it into your GPO and change the certificate service audit settings.auditpol.exe /backup /file:c:\auditsettings.csv
-
-
Hi Vadims
Does the following have any bearing on this particular blog post?
auditpol /set /subcategory:”other system events” /success:enable /failure:enable
It is outlined in a Microsoft article located at https://docs.microsoft.com/en-us/windows/win32/seccng/cng-features
The article includes the following statement
No audit record is generated by kernel mode CNG. Administrators need to configure the audit policy to obtain all KSP audit logs from the security log. An administrator must run the following command line to configure additional audits generated by KSPs:
auditpol /set /subcategory:”other system events” /success:enable /failure:enable
Thanks
-
KSP auditing is a different thing and is not related to this blog post. Normally, you don’t need to audit KSP events, they are only necessary when debugging issues.
-
-
Thanks, Vadims
-
Hi Vladims,
Thanks for sharing!

 Schedule a Demo
Schedule a Demo