Preparing for Microsoft's Strong Certificate Mapping Enforcement – What You Need to Know
Microsoft’s recent update, released on February 11, 2025, significantly changed certificate-based authentication by introducing Strong Certificate Mapping. This update is designed to reduce the risk of credential escalation by enforcing stricter mapping requirements for certificates used in authentication.
Ensuring compliance in organizations that rely on certificate-based authentication is necessary and vital for preventing authentication failures and costly outages. Don’t wait until it’s too late—now is the perfect time to take decisive action and thoroughly review and update your PKI environment.
What Changed on February 11, 2025?
Microsoft’s enforcement requires that certificates used for client authentication include strong mapping information. Certificates at risk consist of those issued via Offline Templates and those used for Wi-Fi authentication, User Logons, VPN access, and MDM-enrolled devices. This also impacts certificates issued through mechanisms such as Microsoft NDES or third-party MDM tools that have yet to be updated to comply with strong mapping. Authentication failures are likely to occur if these certificates do not meet the new Strong Certificate Mapping standards.
Full details can be found here:
Microsoft Support: Certificate-Based Authentication Changes
Temporary Mitigation Available Until September 2025
Though Enforcement Mode is now the default, administrators can temporarily mitigate the impact by enabling Compatibility Mode. This option allows certificates without strong mapping to continue functioning but requires manual configuration by February 11, 2025. However, this is only a short-term solution, as Microsoft will fully implement strong mapping after September 2025.
To enable Compatibility Mode, domain controllers need to be configured by adding a registry key. The linked Microsoft documentation above offers more details on implementation.
How to verify Compatibility Mode:
To check if compatibility mode is enabled on the domain controllers, we can use Regedit.exe’s GUI or the PowerShell command.
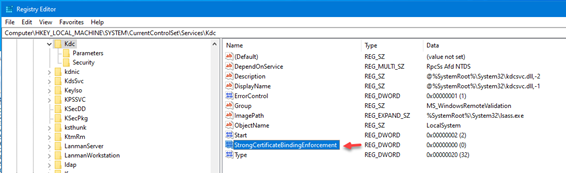
Registry Location: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Kdc
Look for StrongCertificateBindingEnforcement and a value of 0
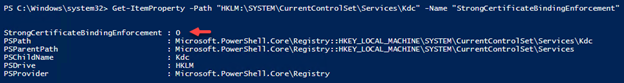
Use PowerShell to get the value:
Get-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Services\Kdc” -Name “StrongCertificateBindingEnforcement”
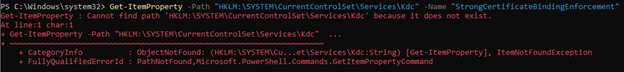
If the domain controller is not configured, there will be no StrongCertificateBindingEnforcement key.
The PowerShell command would return:

Expand Your PKI Visibility
Discover why seeing is securing with revolutionary PKI monitoring and alerting.
Learn More About PKI Spotlight®Enabling Compatibility Mode (Domain Controllers)
If needed, these are the steps to add the registry key to the domain controllers manually.
Regedit Method
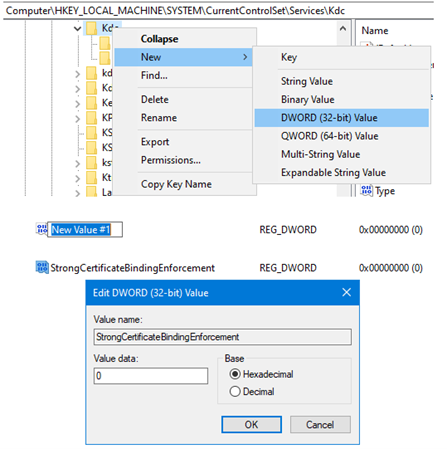
1. Open Regedit.exe, browse to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Kdc
2. Update Registry Key Name to: StrongCertificateBindingEnforcement and leave Value data 0
PowerShell Method
New-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Services\Kdc” -Name “StrongCertificateBindingEnforcement” -Value ”0” -PropertyType “DWORD”
Detecting Strong Certificate Mapping Issues
If authentication issues arise with the certificate mapping, you may encounter Event ID 39, 40, or 41 in the domain controller’s event viewer under System, depending on the operating system involved.
Identifying At-Risk Certificates with PKI Spotlight
Ensuring compliance requires identifying certificate templates that do not meet the new mapping requirements. Instead of manually running complex PowerShell scripts, organizations can leverage PKI Spotlight to audit their certificate template inventory efficiently.
Key Benefits of Using PKI Spotlight:
- Automated Discovery – Instantly identify At Risk Templates
- Comprehensive Visibility – Centralized visibility to all at-risk certificate templates across your environment.
- Streamlined Remediation – Take proactive steps to update certificate issuance processes before enforcement deadlines.
Take Control of Your PKI Security – Try PKI Spotlight Today!
Navigating the complexities of Microsoft’s Strong Certificate Mapping enforcement doesn’t have to be a challenge. PKI Spotlight provides real-time insights and automation to help organizations stay ahead of compliance requirements.
Don’t wait until authentication failures disrupt your operations.
With PKI Spotlight, you can streamline the discovery and remediation process while gaining complete visibility into your vulnerable certificate templates. Schedule a demo today!

 Schedule a Demo
Schedule a Demo