The PKI CryptoGram – Edition #2
July 2015
The PKI CryptoGram #2
PKI Technology Corner
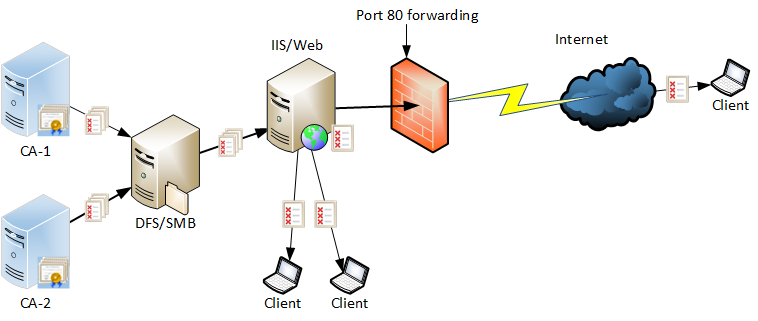
Over the years I have been advocating to customers that core components in a PKI need to be both physically and logically secure. Historically this was easy to address by placing the servers, Hardware Security Modules (HSM), keyboard, monitor and all the other equipment in a dedicated rack in the data center. We could then set up two person controls such that one group of people had a key to the cabinet, another group of people had access to the data center. Policies would be written that indicate one person from each group must be present whenever administrative work needed to be performed on the servers.
Fast forward to today’s typical enterprise where more and more server roles are migrating to virtual machines – generally on VMWare or Hyper-V. How do you implement these same controls when all administrative access to the PKI components is performed remotely with remote desktop services or the hypervisor software?
As part of an ongoing project with a client, an innovative alternative option was found. While it doesn’t match the same level of controls possible when the components are physically isolated, it offered enough control that the client felt it met their security needs. The environment will be protected by PowerBroker (PB) by Beyond Trust for all of the core PKI server roles. The software will manage all of the administrative accounts, and when an administrator needs access to the server, the PB software will require another person to approve their access. Once approved, the user session is brokered into the PKI server. There is no other access method and without the approval, the user is unable to connect (passwords and ports are brokered).
In addition, future capabilities in the PB product will enable a second person to remotely view all activity of the administrator in real time, pause the session if something suspicious is occurring, and then attest and digitally sign a session recording. This will provide an audit log for the server and illustrate two person controls were in place for the lifetime of the CA.
While this lacks some of the controls possible with a physical deployment, such as the ability to fill all access and key ceremonies, it provides an alternative to organization balancing security needs, virtual server efforts and integrity controls.
Products and Services
Qualified Subordination is often a topic that comes up for organizations that want their certificates issued from an internal PKI to be trusted by external customers, clients or partners. Since certificate trust is dependent on a mutually trusted PKI, internal deployments are untrusted outside their managed client base. Uses such as secure email, SSL and network encryption are common scenarios where external trust is important.
Over the last few years, I have seen many of the commercial providers exit the space in offering Qualified Subordination services. This has largely been driven by security and audit requirements that are beyond the ability of most environments. To be clear, this is neither an easy, nor inexpensive proposition to deploy. But for organizations that need it, the small field of providers has been worrisome.
Recently I met with Andrew Pynes, VP of Enterprise Sales at Comodo and was glad to hear that they are still in the business of offering Qualified Subordination. The terms and requirements are extensive, but there is no substitution for a globally trusted provider in these scenarios.
Tips and Tricks
One of the most often asked questions I get is whether it is possible to install the Certificate Authority Web Enrollment (CAWE) website to a server other than the CA to enable manual enrollments without exposing the CA itself. Even though this service hasn’t been modified by Microsoft since Server 2003, it remains extremely popular and used in most environments.
In fact, there is a way to install CAWE on an alternate server. The trick lies in the security configuration of the webserver running CAWE. Since users authenticate themselves to the website, the CAWE server needs to be able to impersonate the user when it performs the enrollment with the CA. To accomplish this, the server must be configured as Trusted for Delegation.
Fortunately, Microsoft does have an article on how to install and configure CAWE on an alternate server (proxy). It was written for Server 2008, but is applicable for all Windows OS version.
ADCS Hotfix & Known Issues Digest
The ADCS Digest continues to grow! Over the last year, what started as a small set of known issues and hotfixes has grown to almost 100 items across the spectrum of Windows Server and client operating system versions. Due to the growth, the Digest has been reorganized into discrete pages for each Windows version to provide better organization and easier reference for you.
In addition to the layout changes, several new items were updated to the list on July 8th, so if you haven’t checked out the list lately, now’s a good time: Hotfix and Known Issues Digest.
ADCS Hotfix Stats Table
UPCOMING EVENTS
PKI In-Depth Training
Los Angeles
Sept 21-25
Training News
Save the date! The new Advanced PKI training class registration will open soon. This class will only be offered twice a year in the U.S., once on the west coast, the second on the east coast. The class will build on the PKI In-Depth course and explore advanced topics such as security, disaster recovery, migrations, management and recovery. Prepare for a week of hands-on lab based learning.
Look for more details shortly, but save these dates:
Portland, Oregon – April 4-8, 2016
Washington, DC – Sept 19-23, 2016
Future CryptoGram Topics
In the next issue of the CryptoGram, look for details on the following topics:
Windows 10 Certificate Changes and Improvements
PKI Solutions Advanced Class Course Outline and Details
Application level certificate verification with Promon Shield
DANE – An RFC to bind SSL certificate identities to DNS names
Related Resources

Mark B. Cooper
President & Founder at PKI Solutions, Leading PKI Cybersecurity Subject Matter Expert, Author, Speaker, Trainer, Microsoft Certified Master.
View All Posts by Mark B. Cooper
 Schedule a Demo
Schedule a Demo