Customer Case Study: Large Gas & Electric Utility Holding Company
The third largest electric utility company in the U.S. selects PKI Solutions to update their organization's PKI environments and implement PKI Spotlight monitoring and alerting.
Download this Case Study More Case StudiesWhy did you choose PKI Solutions?
- PKI Solutions unique expertise with PKI
- Extensive experience with Hardware Security Modules (HSMs)
Business Challenge
As one of the largest utility companies in the U.S., with gas and electric utility holdings spanning several states, this organization’s PKI is mission-critical to their operations and outages can be disastrous. Since the company is operating in a highly regulated industry, its IT team needed to ensure that they maintain secure and highly available PKI environments across their organization’s widespread network of identity and encryption systems.
According to the organization’s senior IT security analyst, parts of the company’s PKI have failed a few times during the past several years due to a number of different events. The organization’s PKI suffered a series of unfortunate events that were all unrelated but all happened in rapid succession one after another. Unfortunately, the organization had a network outage that impacted its network cluster. The IT team discovered that their cybersecurity infrastructure that was reliant on the PKI infrastructure for one of the region of the country where the organization has operations wasn’t configured in a high availability standard as the rest of the system.
“Things seemed to change over the span of two to three months. Unfortunately, this resulted in some high visibility outages which had serious impacts on our organization,” he says. “People don’t realize just how deeply engrained the PKI technology is or how much the business relies on it until it’s not available and there is an outage.”
The outage took down the monitoring of some of the company’s infrastructure. When they lost the PKI infrastructure in one of the regions, most of what was reliant on that infrastructure in that region of the country started to fail. The fixed wireless modems that the IT team had deployed to the organization’s substations and other key critical areas across its footprint failed. Those wireless radios are used to communicate back to the corporate offices through a VPN and that VPN tunnel is authenticated and identity is verified through certificates.
“It was a not a good situation. There was a network outage late one night and there was no way to monitor the thing. So, on Monday morning, not only were we getting alarms that we had lost connectivity to a lot of substations and employees couldn’t get connected via our VPN. Since approximately 50% of our workforce at that time was working remote due to the impact of COVID-19, it was an unfortunate situation,” says the IT security analyst.
It was a bad situation. There was a network outage late on a Friday night and we had no way to monitor the thing. So, on Monday morning, not only were we getting alarms that we had lost connectivity to a lot of substations, but employees couldn’t get connected via our VPN. Since approximately 50% of our workforce is working remote now due to the impact of COVID-19, it was not good.
Having a working VPN is critical to our operations. It wasn’t just the fact that the PKI went down — it also exposed some flaws in our infrastructure outside of our PKI environments as well. Ultimately, we learned a hard lesson that not having a way to monitor the health and security availability of our PKI environment is a key deficiency.
– IT SECURITY ANALYST
Solution Overview
Historically, the organization hadn’t been able to effectively monitor the health of the PKI environment to a degree where its IT team could be proactive instead of reactive. Following the outage, the IT security analyst reached out to PKI Solutions for help.
“Fortunately, I knew that Mark Cooper and PKI Solutions had been working on a monitoring and alerting product. So, rather than reinventing the wheel and trying to develop this in-house ourselves we decided to look into PKI Solutions’ solution for monitoring. After seeing the demo of PKI Spotlight, I was impressed. My leadership team agreed and we decided to work with our trusted business partner PKI Solutions to test out the product in their Early Access Program and get it implemented ASAP.”
Since the organization’s PKI environments are geographically redundant and support a complex environment the IT team had a high need for a robust monitoring and alerting solution. The organization also wanted a solution that was hosted on premises and not a cloud solution. According to the organization’s IT security analyst, “The PKI Solutions team asked me for my wish list of features that I would like to see in the product and I shared some of my needs and business requirements. PKI Spotlight delivered on all of them.”
Key Deliverables
- Provided consulting services to ensure the organization’s Public Key Infrastructure (PKI) is secure and available
- Installed PKI Spotlight for ongoing monitoring and alerting of the organization’s PKI environment
Outcome
Implemented PKI Spotlight to provide real-time monitoring and alerting of the availability, configuration, and security of the organization’s PKI
Results
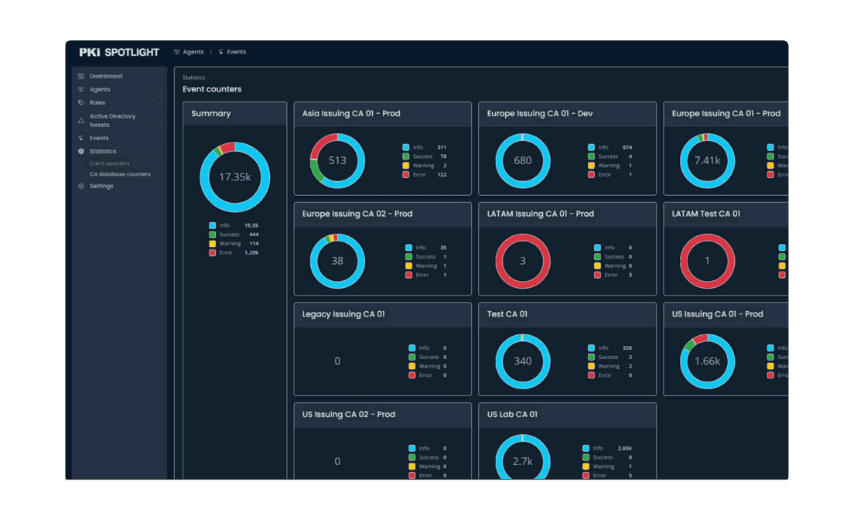
In an effort to increase security, the organization has limited the ability for admins and analysts to log into certain key infrastructure components. The new administrative controls are a critical part of the overall security protocol, but slow the log-in process. Fortunately, having information from all of those individual components presented in PKI Spotlight’s centralized dashboard without users needing to log into each individual component in the PKI environment. In the past, it would take IT team members about 15 minutes to log into each box and with approximately 10 components that adds up to more than an hour spent logging into all of those components. Thanks to PKI Spotlight’s centralized dashboard, it is a huge timesaver for users. The alerting features also allow users to receive alerts to potential problems and quickly take corrective action.
“PKI Spotlight has exceeded my expectations and it is important to our business. I’m confident in the product development because I know that the team at PKI Solutions really ‘gets’ it because they are the experts in PKI,” says the organization’s IT security analyst. “They did a great job of managing the Early Access Program process and responding to my requests for any minor hiccups that developed.”
“PKI is foundational and a cornerstone technology for all companies. We anticipate that our company’s dependency on PKI services could increase over time. PKI Spotlight helps us introduce additional resiliency in our identity and encryption infrastructure and stay ahead of situations that can cause issues with our business,” says the IT security analyst. “PKI Spotlight is unique as there is nothing in the market that focuses solely on PKI, and we have been able to quickly see value. We now have a centralized view of status, configurations, and events. With notifications and alerts, all stakeholders that are dependent on the PKI will have visibility into the operational status. It also frees our team to focus on high value tasks critical to risk reduction.”
-
Get to Know PKI Spotlight!
Schedule a demo with our PKI experts to learn how PKI Spotlight addresses the most common challenges faced by our customers.
By the end of your call, you’ll have a clear understanding of how PKI Spotlight will improve your operational resilience, security posture, threat detection, and best-practice capabilities.
Topics we will cover:
- How the real-time aggregation engine works to process information from PKI roles such as CAs, CRL distribution points, Hardware Security Modules, and more.
- How to set up monitoring and alerting rules so that you, your teams, and stakeholders can get notified on changes, failures, and even pre-failure states.
- How to use config explorer to get insights into PKI configurations such as CA permissions, revocations, and crypto modules.
- How you can use time-based filtering to keep track of trends and establish behavioral baselines.

 Schedule a Demo
Schedule a Demo