Securing the World’s Leading Companies
Answer a Few Questions to find a Solution for your Use Case
PKI Spotlight
PKI Spotlight
PKI Spotlight addresses security threats from across your enterprise, from visibility into PKI issues found in audits, to increased availability of all PKI and Hardware Security Module (HSM) environments. Consolidate real-time monitoring and alerting to act decisively and maintain excellent PKI hygiene. PKI Solutions helps you visualize and optimize the outcomes that matter to you.
Learn MorePKI Solutions by the Numbers
-
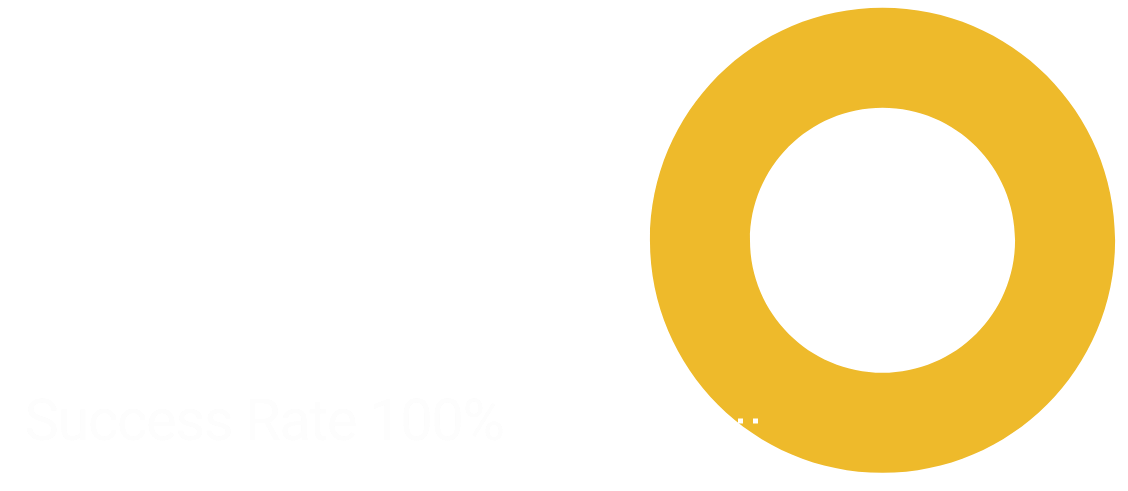
SUCCESSFULLY PASSED PEN TESTS 100 %
PKI Spotlight enables a 100% pass rate for PKI in penetration tests, so enterprises can rest easily knowing their PKI is secure.
-
Combined Years of PKI Experience 70
With decades of experience and active participation in shaping the PKI environment, PKI Solutions can help you build and maintain preparation for what’s ahead.
-
PKI Projects Completed 300 +
PKI Solutions has experience with your industry and in similar types of environments.
-
PKI Training Students 1000 +
Elevate your expertise with the experts. Our extensive training programs are built on our experience and your needs.
Why PKI Solutions?
-
PKI Spotlight gives us productivity gains and peace of mind that our PKI systems are available and functional, and any service that relies on our PKI operates smoothly and securely. With PKI Solutions, we get best-in-class expertise.

Connect With Us for Certainty in Security
If you’re ready to learn more about our essential solutions for your essential PKI, reach out today. Book time with one of our specialists to discuss your needs and how we can meet and exceed your business requirements.
CONTACT US
Email: hello@pkisolutions.com
Phone: +1 (971) 231-5523
Corporate Headquarters
5331 S. Macadam Ave, Suite 330
Portland, Oregon 97239


 Schedule a Demo
Schedule a Demo